Regulatory Compliance Assessment

The USProTech GRC application provides a solution that is both manageable and scalable in today’s quickly changing technology landscape, while going beyond the mere letter of the law to comply with best business practices in general.
The US ProTech GRC application is able to enable the regular examination of:
- Comprehensive NIST 800-171 Assessment / Remote Collaboration & Application
- External IP Scanning / US ProSecure (NIST 800-53)
- Internal IP Scanning / US ProSecure (NIST 800-53)
- Active Directory Scanning / US ProAd (NIST 800-171)
- Data Breach Risk Intelligence Report / US ProScan (NIST 800-171)
- Current Governance, Risk & Compliance Capabilities / GRC Application & Tools
- Review: Policies and Procedures / (NIST 800-171 all 14 Control Families)
- Complete SSP (System Security Plan) Documentation / GRC Framework
- Deliver POAM (Plan of Action-Monitored) / GRC Framework
Below you will see an example of the level of detail our GRC can provide when performing ongoing compliance.
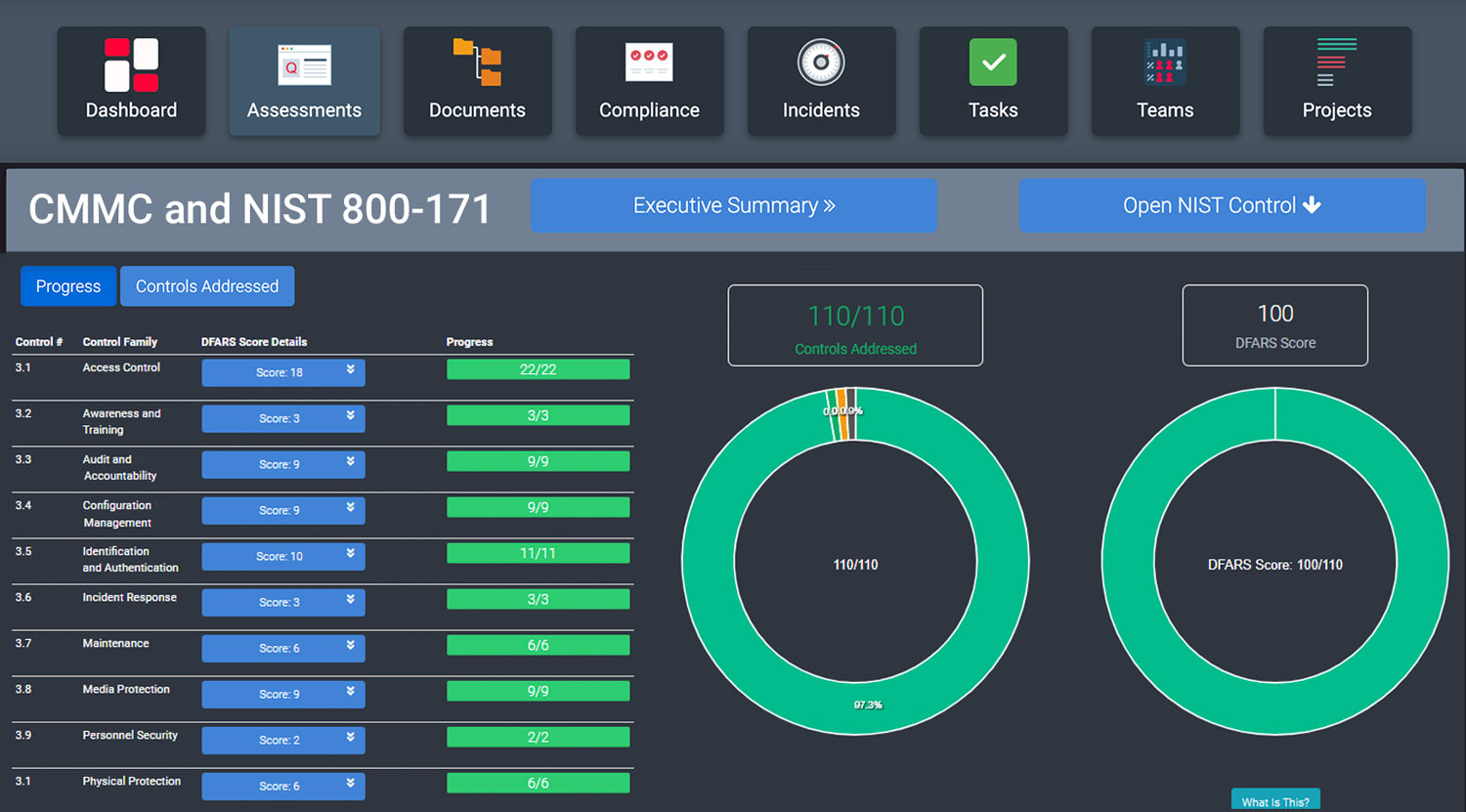
Evaluate the value of this information for yourself! Samples are available for you below.
HIPAA and PCI specialized
Experience you can trust!
If you operate within a regulated industry, you know the importance of having a reliable partner who understands the complexities of your environment, someone to whom you can confidently delegate those issues, so that you can get on with your business.
For 15 years, we’ve been working with medium to large size businesses in specific industries including healthcare, banking/finance, petro-chemical, organized labor and retail which has allowed us to gain in-depth knowledge of the industry-specific and federal regulations – particularly the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA) – which typically affect our clients.
For businesses and organizations of any size, US ProTech will identify gaps between current security posture and industry-specific regulations like PCI DSS and government regulations such as HIPAA. Our assessments provide the following:
- Benchmarking
- Executive summary report comparing past examination to current security controls
- Gap Analysis
- Measure of existing security posture against different types of regulations
- Risk Assessment
- Details of weaknesses and risks with easy to read numerical representations
- Remediation Report
- Details of the required actions to bring security controls in line with acceptable standards
Accreditations
Federal Regulatory Compliance is a specialty of US ProTech: we offer comprehensive policies, procedures and processes, all of which have enabled us to become officially validated by the U.S. Department of Commerce to exceed the High Impact Baseline standards of N.I.S.T. 800-53. Furthermore the comprehensive US ProSecure provides verification of meeting and exceeding strict internet technology security related standards for other federal mandates such as HIPAA, PCI, SOX, ISO, etc.
The process used by US ProTech applies to both IP based targets and web applications alike. It also provides standardization benefits of Security Content Automation Protocol (SCAP), a U.S. Government mandated initiative, all of which is part of the Joint Task Force Transformation Initiative for High-Impact Baseline systems as part of the national directive to adopt a single standard concerning Internet security standards, and the protection of data, personal or otherwise.
Dissimilar to other network scanning tools, US ProSecure identifies all known vulnerabilities through the U.S. National Database and provides 12 different reports/summaries and “where to read more about” each Web App or IP address issue.
Regulatory Compliance Audit Types
1. PCI PAN Scans:
Test for unencrypted payment card data on your system to ensure that no improper application configuration or accidental storage of payment-card information on Word or Excel is threatening your compliance to PCI DSS. For a PCI PAN Scan sample, see below (under Regulatory Compliance Assessments Samples).
2. Gap Analysis:
US ProTech’s Bench-Marked Gap Analysis reports take you through every single aspect of your regulatory compliance posture. Every item of the law is examined and compared to what your current situation is. It the most comprehensive report you can imagine and includes all the other types of assessments described below. For a HIPAA Gap Analysis Report sample, see below (under Regulatory Compliance Assessments Samples).
3. Networks scans:
External scanning: Perhaps the most common type of network scan, this is where we test your vulnerability from an outsider’s perspective. This means that we try to find how well your security will uphold against someone from outside your company attempting to find a way in.
Internal scanning: Did you know that 70% of your network attack surface is internal? In other words, you are potentially most vulnerable from within your own network. This is why internal scanning is so important to ensure you operate at the highest levels of security.
Unauthenticated scanning: In this case, we assess your vulnerabilities from the perspective of someone who doesn’t have credentials. This is mainly helpful to find basic configuration issues or input and output validation type errors
Authenticated scanning: This type of scan tests your system’s vulnerabilities against attacks from someone who has credentials to your network. Since authenticated scanning gets “inside” your system, it allows for privilege escalation attack checks and the discovery of any business logic flaws that could become security defects.
Penetration & wireless testing:
Take the network security evaluation one step beyond by searching for ways to exploit potential vulnerabilities in the same way that anyone attempting to attack your system would. With the US ProSecure penetration testing tool and the efforts of our highly qualified experts, we are able to assess your true security posture and make sure that no cracks, however small, are ignored.
Web application scanning:
These tests, vital for companies which use web applications in their day-to-day operations, are a type of penetration test specifically adapted to these applications instead of traditional networks.
Physical audits:
Physical security is the first line of defense for any device or system and is therefore of the utmost importance. For this reason, US ProTech conducts physical audits which include step-by-step guides and comprehensive documentation, to ensure both regulatory compliance and best business practices are met.
Regulatory Compliance Assessments Samples
[wpdm_file id=33]
* Please note that the free report does not provide Gap Analysis to HIPAA Ominbus 3.0, and that it is a shortened sample. To view the full report, please fill out the form on the right.
Other Free Materials:
Full HIPAA Gap Analysis Report: get the full-length report and see for yourself how detailed it is! Simply fill out the form on the right!
HIPAA Security Advisory: a short white paper which takes a look at the current Security Posture of the Healthcare industry and what can be done to improve it. Simply fill out the form on the right to receive it.
For more information on Regulatory Compliance Assessments or to get a quote, fill out the form on the right, or call us today!

