
Mar 26, 2025 | Technology News
Please join Cybersecurity Practitioners and Military Experts for a Deep-Dive into some of our Nation’s most significant data breaches, the recent high-Alert notification from the FBI. This Webinar will discuss in detail the key findings from the latest FBI Report concerning weird ransomware attack threats delivered by the United States Postal Service, (yes really), alongside a dangerous ransomware campaign from so-called Ghost attackers, and some of the most sophisticated threats against Gmail users ever.
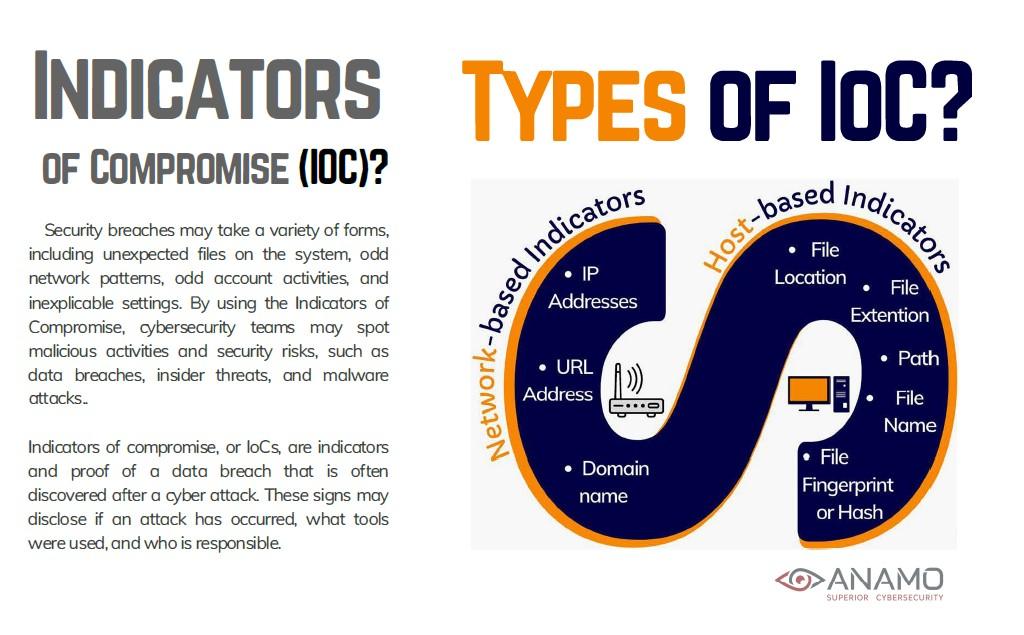
Mar 26, 2025 | Technology News
In cybersecurity, an Indicator of Compromise (IoC) is evidence suggesting a system or network may have been breached, helping security teams identify and respond to potential or ongoing attacks is exactly what US ProTech delivers with its Anamo CDM software that correlates Host-Based Indicators with comparative HashID Analytics.

Feb 14, 2025 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Numerous platforms are available today for business telecommunications, enabling businesses to seamlessly interact with customers. With data constantly transferred from servers to devices, data security remains a crucial concern. Read on to learn about communicating and collaborating while keeping data secure.

Feb 10, 2025 | CDM, Continuous Diagnostics & Mitigation
Join the U.S. Office of the Department of National Intelligence (ODNI) and US ProTech, for a Deep-Dive to one of the Nation’s most significant data breaches, the recent compromise of the U.S. Department of Treasury.

Feb 6, 2025 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Software as a Service (SaaS), a platform supporting office work through applications available from MS 365 and other software, enables companies to communicate, collaborate and drive business outcomes. Companies using SaaS applications need to backup critical workload to ensure comprehensive data protection. Read on to learn what SaaS Backup has to offer to protect your valuable data.

Jan 21, 2025 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Fifth Generation (5G) networks can expand data capacity, bandwidth and boost reliability. Read on to learn more about how the expansion of 5G networks can enhance your business telecommunications and improve user experience, and the role cybersecurity plays.

Jan 14, 2025 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Chatbots, also termed conversational AI (artificial intelligence), have made AI more popular than ever. They can help with simple tasks, though AI agents have greater power and a wider range of use cases. Read on to learn more about the prospective move from chatbots to AI agents to provide a better user experience as well as save time and money.
Dec 19, 2024 | Technology News
Weekly summary of discussions, and best practices on topics such as ransomware, ZTA Admin with Anamo, and recent Cybersecurity related events.
Krispy Kreme Cyberattack Disrupts Online Orders, Impacts US Operations
Krispy Kreme announced a cyberattack on November 29, 2024, affecting its online ordering system and causing operational disruptions.
Dec 19, 2024 | News, Technology News
Anamo CDM Cybersecurity Presents:
The US Convergence of Cybersecurity and the Industrialization of Space in the Quantum Age
Panel from DoD, DNI, Pentagon, Microsoft Security Center, and US ProTech

Dec 10, 2024 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Cybersecurity, more than just being about tools, is about people. People can, on the one hand, be a weak link in your company’s cybersecurity chain. On the other hand, if they understand the importance of cybersecurity to your organization, as well as what it means for them personally, they can be an asset. Read on to learn more about making cybersecurity a business decision as well as part of your company culture,
Page 1 of 3112345...102030...»Last »








